Now Reading: Challenges of Cloud Migration and How to Mitigate Them
-
01
Challenges of Cloud Migration and How to Mitigate Them
Challenges of Cloud Migration and How to Mitigate Them
Executive Overview
Cloud migration promises scalability, cost efficiency, and business agility, but enterprises routinely confront a set of recurring obstacles. Data gravity, complex interdependencies, and the risk of service disruption can slow progress and erode stakeholder confidence if not managed deliberately. A successful migration requires alignment across security, operations, and business continuity teams, plus a practical plan for testing, validation, and rollback.
This article distills the most common challenges into actionable categories and pairs them with pragmatic mitigations designed for large-scale, multi-cloud environments. While every journey is unique, the patterns described here help leaders set realistic timelines, allocate resources, and measure readiness in a way that keeps critical services available and compliant while migrating workloads to the cloud.
Downtime and Cutover Planning
Downtime can translate into lost revenue, customer dissatisfaction, and regulatory penalties, especially for public-facing services and latency-sensitive workloads. The real risk isn’t only the duration of the outage but the ripple effects on data consistency, user analytics, and integrations with downstream systems. A migration plan should differentiate between planned downtime during cutover and the short blips that occur during normal operations, and it should minimize both through staged deployment and rigorous testing.
The following practices are essential when preparing for go-live:
- Establish a dedicated cutover window with business owners, service owners, and incident response teams.
- Use blue/green or canary deployment models to minimize user impact and provide rapid rollback.
- Run thorough pre-cutover validation, end-to-end tests, and data reconciliation checks in a staging environment.
- Implement automated smoke tests and synthetic transactions to verify critical paths after the cutover.
- Prepare automated rollback scripts, clearly defined escalation paths, and runbooks that document contingency actions.
- Keep a live, documented plan for post-cutover monitoring and issue triage to detect and recover from early failures quickly.
Data Transfer and Migration Methods
Moving data between environments presents challenges around bandwidth, latency, consistency, and integrity. To minimize risk, teams should address data synchronization, identity, encryption, and the order of operations between source and destination. Planning must account for data growth during migration and the possibility of delta transfers, reconciliation, and acceptance testing across systems.
Choose an approach that balances speed, cost, and cloud fit. The common migration strategies include the following:
- Lift-and-shift (rehost): migrate applications with minimal changes to achieve faster time-to-value, preserving architecture while moving to a new environment.
- Replatforming (lift, tinker, shift): make targeted optimizations to exploit cloud-native services without a complete rewrite.
- Refactoring (re-architect): redesign workloads to maximize cloud-native capabilities, scalability, and resilience, accepting longer timelines and greater coordination.
- Phased data migration with continuous replication: keep source and target in sync while gradually shifting workloads to reduce risk.
Security and Compliance in Cloud Migration
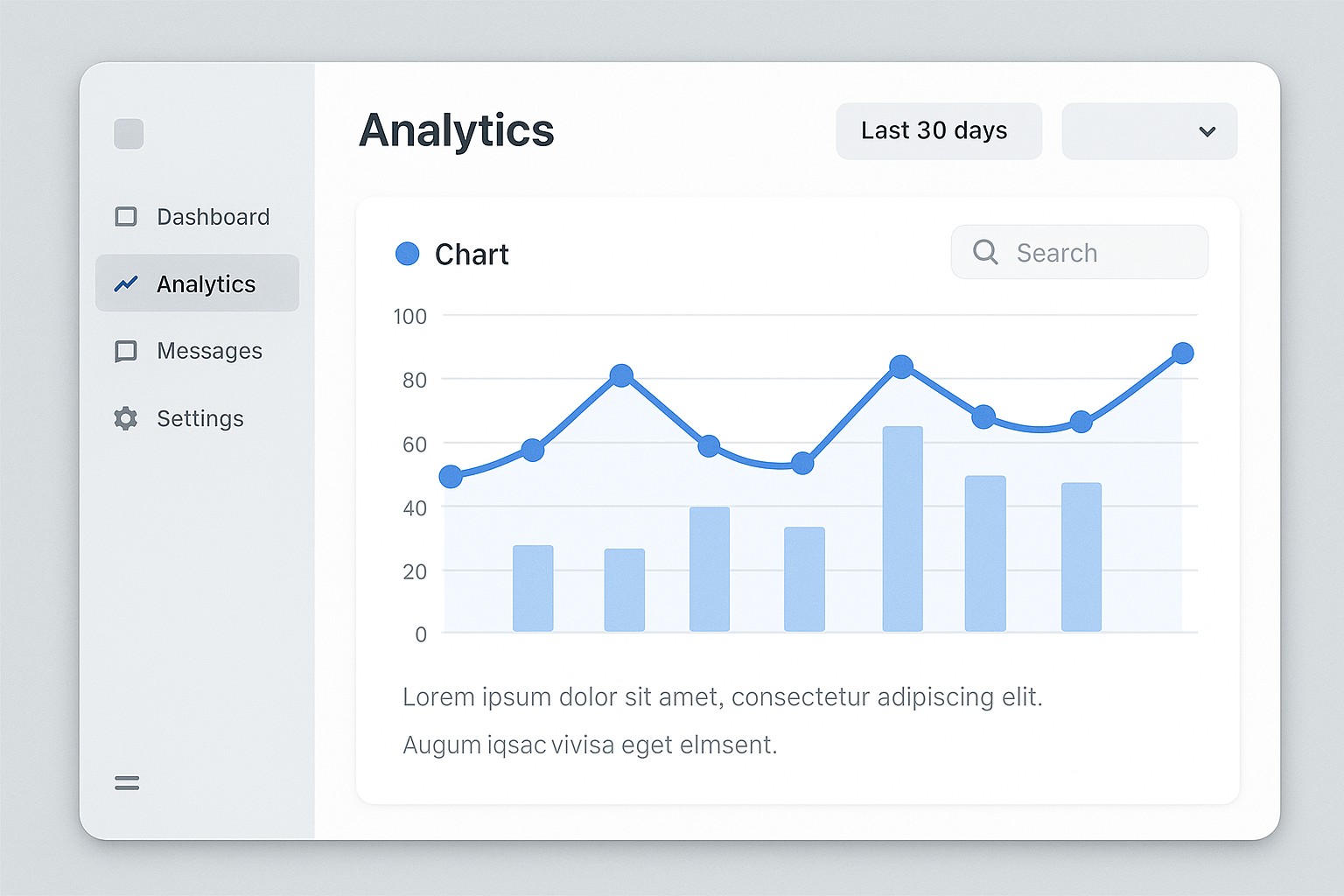
Security must be designed in from the start, not added as an afterthought. Migration introduces new network boundaries, identity surfaces, and data exposure points that can undermine posture if not carefully managed. Common risks include misconfigured access, drift in security controls, and gaps in data protection during transit and at rest.
Mitigation involves disciplined governance, automation, and ongoing validation. A pragmatic approach combines policy-driven controls, continuous monitoring, and a clear mapping of regulatory obligations to technical controls. In particular, consider standardizing around centralized identity, encryption, and threat detection, and remember to test regularly by simulating incidents and recovery scenarios. automate multicloud security steps is a practical emphasis for teams working across multiple clouds.
- Enforce least-privilege access with centralized IAM.
- Encrypt data in transit and at rest; manage keys with a centralized KMS.
- Enable network segmentation and micro-segmentation to limit blast radius.
- Implement continuous monitoring, anomaly detection, and alerting to detect atypical activity.
- Automate configuration drift detection and remediation to maintain compliance over time.
- Apply policy as code and automated compliance checks to enforce consistent standards across clouds.
Operational Readiness, Governance, and Cost Management
After migration, sustaining reliability requires clear operating models, governance, and cost discipline. Define ownership for cloud-native services, establish runbooks for incident response, and create a feedback loop that ties operational data to improvement initiatives. Use standardized incident categorization, post-incident reviews, and agreed SLAs to keep teams aligned and focused on preventing regressions.
Cost control emerges as a continuous discipline, not a one-time activity. Tagging, budgets, and reserved instances, along with ongoing optimization of idle resources and scalable architectures, help ensure that the cloud investment remains aligned with business goals. A governance framework that enforces policy, controls spending, and documents change impact reduces the risk of uncontrolled drift.
People, Skills, and Change Management
Technology alone does not guarantee migration success. Organizations must address people and process, ensuring the right skill sets, knowledge transfer, and cross-functional collaboration. Engaging product owners, security teams, and operations early helps surface edge cases and drive ownership, while training programs accelerate adoption of cloud-native patterns.
A practical change program includes clear roles, hands-on labs, and a phased competency roadmap that aligns with the migration milestones. Leaders should sponsor regular knowledge sharing, documentation, and a culture of continuous improvement to sustain momentum after the initial go-live.
FAQ
What is the most critical challenge in cloud migration?
There isn’t a single universal critical challenge; however, alignment across teams, data dependencies, and governance often determine the pace and success of a migration. Without clear ownership, consistent security controls, and a plan for data integrity and interoperability, projects stall. Early focus on defining responsibilities, data mappings, and a testing-and-rollback strategy tends to reduce risk and accelerate progress.
How can we mitigate downtime during migration?
Mitigation centers on rigorous planning and scalable deployment models. Use phased cutover with blue/green or canary approaches, maintain synchronized data between source and target during transition, perform extensive pre-cutover testing, and have automated rollback procedures ready. Clear incident response playbooks and continuous monitoring after cutover help detect and recover from issues quickly, minimizing business impact.
What are best practices for data migration in multi-cloud environments?
Best practices include establishing a data governance framework, choosing appropriate data replication and synchronization methods, and ensuring end-to-end encryption and integrity checks. Define a data schema and mapping strategy early, validate data quality continuously, and plan for delta transfers to keep sources and destinations in sync. Regular reconciliation and acceptance testing across clouds reduce surprises during go-live.
How do we maintain security and compliance during and after migration?
Maintain security by design through centralized identity, consistent access controls, and automated policy enforcement across clouds. Implement encryption at rest and in transit with unified key management, enforce network segmentation, and continuously monitor for drift and anomalies. Treat compliance as a continuous process with policy as code, automated audits, and regular tabletop exercises to validate readiness.
How long does a typical cloud migration take and what affects the duration?
Durations vary widely based on scope, complexity, data volume, and the degree of refactoring required. Factors include the number of workloads, interdependencies, the need for security hardening, integration with on-prem systems, and the level of organizational change management required. A typical migration with moderate refactoring and multi-cloud considerations often spans several quarters, with detailed milestones that align to business priorities and governance readiness.