Now Reading: Cloud vs On-Premises Security: Which is Safer?
-
01
Cloud vs On-Premises Security: Which is Safer?
Cloud vs On-Premises Security: Which is Safer?

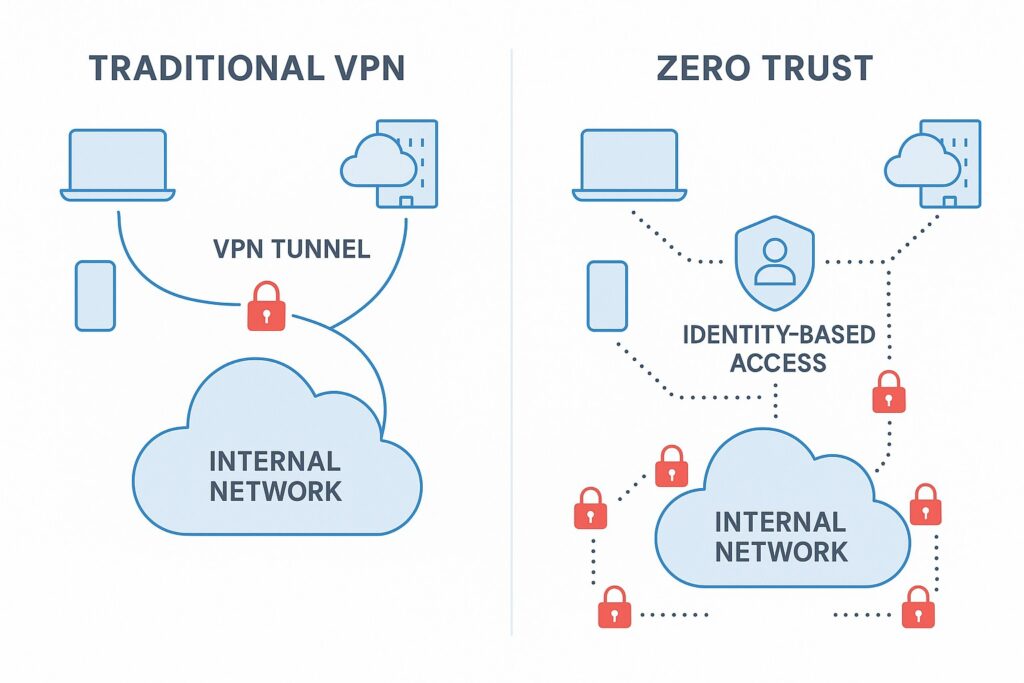
Understanding the Shared Responsibility Model
In cloud deployments, responsibility for security is divided between the cloud provider and the customer. The provider secures the underlying infrastructure—physical data centers, hardware, network fabric, storage arrays, firmware, and the foundational virtualization and platform layers. The customer, in turn, is responsible for everything that runs above that layer: protecting data, ensuring proper identity and access controls, securing applications, and configuring the cloud services in a manner that aligns with policy and risk appetite. The exact split varies by service model. With IaaS, the customer gains control over the operating system and applications, but must still rely on the provider for the security of the infrastructure. With PaaS and SaaS, the provider assumes more of the stack responsibility, while the customer focuses on data governance and access controls. This model is not a one-time decision; it is an ongoing governance discipline that requires explicit mapping of controls, continuous validation, and alignment with compliance requirements.
Understanding this division is essential for risk assessment, vendor management, and compliance. A misstep in governance—such as assuming the provider handles everything or failing to configure strong access controls—can lead to material risk. Organizations should codify the shared responsibility in policy, translate it into technical controls, and establish ownership for configuration reviews, change management, and incident response. In practice, this means maintaining clear runbooks, publishing an inventory of cloud resources, and conducting regular risk and control testing across both cloud and on-premises environments.
- Provider responsibility: physical security of data centers, power and cooling, hardware maintenance, network backbone, baseline infrastructure security, and managed platform security at the virtualization layer.
- Customer responsibility: data protection (encryption in transit and at rest), key management, identity and access management, secure software configurations, patching of guest systems, and security monitoring on their workloads.
- Shared governance: policy enforcement, risk assessment, and compliance oversight to ensure alignment with regulatory requirements across environments.
Threat Landscape: Cloud versus On-Prem
Threats in cloud and on-prem environments reflect differences in control boundaries, visibility, and operational tempo. Cloud platforms create a rich set of capabilities and a shared security model that can accelerate innovation, but misconfigurations—such as open storage buckets, overly permissive API access, or weak identity hygiene—often remain the leading cause of incidents. In contrast, on-premises environments tend to expose risks tied to physical access, aging equipment, manual patch processes, and inconsistent monitoring across network tiers. The best defense recognizes those differences and enforces consistent security patterns across both modes.
Both paradigms confront data leakage, insider risk, supply chain vulnerabilities, and ransomware in some form. The cloud can magnify risk if data is moved without proper classification and encryption; on-prem environments can amplify risk when segmentation and backups are poorly designed. A comprehensive risk view should address data location, regulatory obligations, access controls, and the ability to observe and respond to threats across multiple environments. This requires a unified security program, not separate silos for cloud and data center security.
- Misconfigurations and policy drift: overly permissive IAM roles, public storage buckets, and lax network security groups.
- Access and identity risks: compromised credentials, lack of MFA, inadequate privilege management.
- Data leakage and insufficient encryption: unencrypted or poorly protected data at rest or in transit.
- Supply-chain and third-party risk: dependencies on vendor security practices and software components.
- Ransomware and availability threats: backups, encryption, and network segmentation challenges.
- Physical security and environmental threats (for on-prem): tampering, power outages, and disasters that affect data centers.
Security Controls in Cloud Environments
Cloud environments offer powerful security controls and automation features that support rapid deployment and elasticity, but they also demand disciplined configuration management and continuous posture monitoring. With cloud, you design policy once and expect the platform to enforce it at scale; with human operators, you must guard against drift, misconfigurations, and privilege abuse.
Key controls include identity and access management, encryption of data at rest and in transit, network controls and segmentation, monitoring and logging, and compliance automation. These controls are most effective when they are implemented as a closed loop: policy definitions feed automation, which enforce configurations, generate alerts, and drive incident response.
- Identity and access management: enforce least privilege, MFA, RBAC/ABAC, and conditional access policies.
- Data protection and key management: at-rest and in-transit encryption, central KMS, key rotation, and separation of duties between encryption and key access.
- Configuration, monitoring, and incident response: security posture management, continuous logging and alerting, vulnerability scanning, automated playbooks, and cross-service visibility.
Security Controls in On-Premises Environments
On-premises security relies on a combination of physical security measures, network architecture, and disciplined IT operations. Physical controls such as access badges, visitor management, CCTV, and secure machine rooms remain critical for protecting equipment. Network security requires robust segmentation, firewalling, intrusion detection, and strict change control. Other essential controls include disciplined patch management, baseline configurations, asset management, and tested backups and disaster recovery procedures. Regular drills, like tabletop exercises and failover tests, help ensure that teams respond effectively to incidents. In many organizations, on-prem security is the anchor of the broader risk posture, and the lessons learned here scale to cloud environments through shared governance and unified policy.
Decision Factors: When to Choose Cloud or On-Prem
Organizations weigh regulatory constraints, data residency, and the organization’s tolerance for risk and complexity when deciding where workloads should reside. If data must remain within certain jurisdictions, or if customers require direct control over physical infrastructure, on-prem or a private cloud may be more appropriate. If rapid scaling, global reach, and a pay-as-you-go model align with strategic goals, cloud provides compelling advantages. Hybrid and multi-cloud architectures allow organizations to mix approaches, leveraging the strengths of each, while maintaining consistent security and governance. The key is to standardize control planes, enforce visibility into data flows, and ensure that cross-environment policies are coherent, auditable, and testable.
Operational Considerations: Monitoring, Compliance, and Audit
Effective security in either environment requires robust monitoring, audit readiness, and ongoing governance alignment with applicable standards such as ISO 27001, SOC 2, PCI-DSS, and regional privacy laws. Security teams should implement centralized logging, security incident and event management (SIEM) coverage, and automated compliance reporting. Regular vulnerability management and penetration testing should occur across both cloud and on-prem stacks. Additionally, organizations should invest in resilience: secure backups, tested recovery plans, and well-documented incident response playbooks. Continuous improvement is critical; after every incident or near-miss, teams should review root causes, update control configurations, and adjust training programs.
FAQ
What are the core security differences between cloud and on-premises?
The core difference is who owns and manages various layers of the stack. In cloud, the provider handles the underlying infrastructure and foundational services, while the customer retains control over data, identities, and configurations. In on-premises deployments, the organization maintains end-to-end control of hardware, software, networks, and data, which means greater control but also greater responsibility for everything from physical security to patch management and incident response.
How should organizations approach risk assessment when choosing between cloud and on-prem?
Begin with a data-centric risk assessment that identifies data classifications, regulatory requirements, and exposure risks. Map controls to the shared responsibility model, evaluate vendor security postures, and consider a phased approach such as hybrid or multi-cloud with strong governance and continuous monitoring. Ensure that risk owners, security teams, and IT operations are aligned on policies and incident response responsibilities across environments.
What practical steps can teams take to strengthen security in either environment?
Implement robust identity and access management with MFA and least privilege, encrypt data at rest and in transit, maintain continuous monitoring and logging, perform regular patching and vulnerability management, and test incident response and disaster recovery plans. Foster a culture of secure-by-default configurations and automate where possible to reduce human error and drift.
How does regulatory compliance influence the choice?
Compliance requirements often dictate data residency, access controls, auditing, and reporting. Some regulations impose constraints that are better suited to either cloud or on-prem solutions, while others permit flexible architectures with robust evidence of controls. Organizations should map regulatory obligations to the chosen service model, ensure auditable controls, and maintain transparent, automated reporting to evidence compliance during audits.