Now Reading: Data Privacy vs Data Security: Why Both Matter
-
01
Data Privacy vs Data Security: Why Both Matter
Data Privacy vs Data Security: Why Both Matter
Overview: Data Privacy vs Data Security
In modern enterprises, data is both an asset and a potential liability. Data privacy and data security operate in tandem to protect people and organizations, but they focus on different aspects of protection. Data privacy governs the appropriate collection, usage, and sharing of personal information, ensuring that individuals retain control over how their data is used. Data security, by contrast, focuses on safeguarding data from unauthorized access, alteration, or loss, through technical controls, processes, and governance.
This article unpacks the distinction between privacy and security, explains how they intersect in everyday operations, and provides practical guidance for organizations seeking to address both dimensions in a cohesive program. Throughout, the emphasis is on real-world implications for intranets, collaboration platforms, and other internal systems where personal data and sensitive information circulate.
What is Data Privacy?
Data privacy is the governance framework that determines how personal data is collected, stored, used, disclosed, and retained. It centers on the rights of individuals and the purposes for which organizations may process data. Core concepts include purpose limitation, consent management, data minimization, data subject rights (such as access, correction, and erasure), and transparency about how data flows through systems. In practice, privacy demands that organizations articulate the legitimate purposes of data processing and implement controls that align with those purposes.
Beyond policy, privacy requires operational discipline. Organizations must map data flows, evaluate the necessity of each data element, and establish processes to honor requests from data subjects. The privacy program also encompasses training, governance structures, and vendor management to ensure third parties handle data in ways that respect user rights and regulatory expectations.
What is Data Security?
Data security encompasses the technical, physical, and administrative measures designed to protect data from unauthorized access, disclosure, alteration, and destruction. This includes encryption for data at rest and in transit, robust authentication and access control, network segmentation, monitoring for unusual activity, and incident response planning. Security aims to reduce the likelihood and impact of breaches, ensuring that even if data is accessed, it remains protected and usable only by authorized individuals.
Security programs operate across the data lifecycle, from secure data collection and storage to protected sharing and secure destruction. They require ongoing risk assessment, vulnerability management, and resilience planning to address evolving threats and complex system landscapes, such as those prevalent in intranet ecosystems and enterprise collaboration platforms.
Key Differences Between Privacy and Security
Privacy and security are complementary but distinct disciplines. A structured view helps organizations allocate responsibility, measure progress, and avoid false trade-offs between compliance and protection. The following table contrasts the two perspectives across the most relevant dimensions.
| Dimension | Data Privacy | Data Security |
|---|---|---|
| Primary focus | Governance of how data is used, shared, and retained | Protection of data from unauthorized access and exposure |
| Key controls | Policies on consent, minimization, retention. Rights management. | |
| Stakeholders | Data subjects, legal/compliance teams, privacy officers | |
| Typical activities | DPIAs, data inventories, privacy notices, subject access requests | |
| Metrics | Consent rates, data subject rights fulfillment, data minimization levels | |
| Regulatory emphasis | Privacy regulations (e.g., GDPR, CCPA) | |
| Security outcome | Trust and lawful data use | |
| Security outcome | Confidentiality, integrity, and availability of data |
Data privacy and data security reinforce each other. A privacy program is more effective when security controls reduce the risk of privacy violations, while a security program is more meaningful when privacy considerations drive the selection and configuration of protective measures. In intranet environments, the overlap is particularly visible in access controls, data retention practices, and the handling of employee and contractor information.
Data Governance and Lifecycle Considerations
Data assets move through a lifecycle that begins with collection and ends with disposal. Across that lifecycle, privacy and security requirements should be embedded at every stage. Data minimization and purpose specification should guide what is collected and why, while encryption, authentication, and access controls guard how it exists and who can interact with it. Retention schedules must align with both legal obligations and business needs, with clear deletion processes that render data irrecoverable when appropriate.
Establishing clear data ownership is essential. Data owners define purposes, retention windows, and access rules; data stewards monitor compliance and enforce controls. A data catalog can provide visibility into data elements, their sensitivity, and the applicable privacy and security requirements. This governance infrastructure supports consistent decision-making, reduces shadow data, and enables faster response to both privacy requests and security incidents.
Regulatory Landscape and Compliance
Regulatory requirements shape both privacy and security programs. Regulations such as the European Union’s General Data Protection Regulation (GDPR), the California Consumer Privacy Act (CCPA), HIPAA for health information in the United States, and other regional frameworks impose duties around consent, data subject rights, breach notification, and vendor management. Cross-border data transfers raise additional considerations, including transfer mechanisms and data localization requirements. Compliance also extends to sector-specific standards like PCI DSS for payment card data and industry-specific privacy rules for financial services.
For organizations with intranets and internal collaboration tools, compliance means mapping regulatory obligations to concrete practices: data mapping and DPIAs, documented lawful bases for processing, robust incident response plans, third-party risk management, and ongoing training. The granular implementation of privacy controls often intersects with security controls, making a unified program essential rather than parallel, disjoint efforts.
Practical Strategies for Organizations
A practical privacy-and-security strategy begins with a risk-based approach, aligned to business objectives and regulatory expectations. Start from the data you have, what you do with it, and who can access it. Then design controls that are fit for purpose, scalable, and auditable. The goal is not to chase compliance for its own sake, but to enable trustworthy data flows that support value-generating activities while minimizing risk.
Key privacy controls include:
- Data minimization: collect only what is necessary for defined purposes
- Purpose limitation and DPIA-driven decision making
- Consent management and clear privacy notices
- Access controls and least-privilege principles for intranet systems
- Data retention and secure deletion procedures
- Processes for data subject rights requests and timely responses
Teams should integrate privacy and security into policy design, system architecture, and daily operations. Regular risk assessments, tabletop exercises, and cross-functional collaboration between IT, security, legal, and business units help ensure that privacy and security considerations remain synchronized as technology and processes evolve.
Security Controls and Data Protection Techniques
A strong security foundation is built on layered controls that protect data at rest, in transit, and in use. Technical controls should be selected with an eye toward user productivity, data accessibility, and risk posture. The following structured set of controls serves as a practical baseline.
- Identity and access management (IAM) with multi-factor authentication and least privilege
- Encryption for data at rest and in transit, and key management best practices
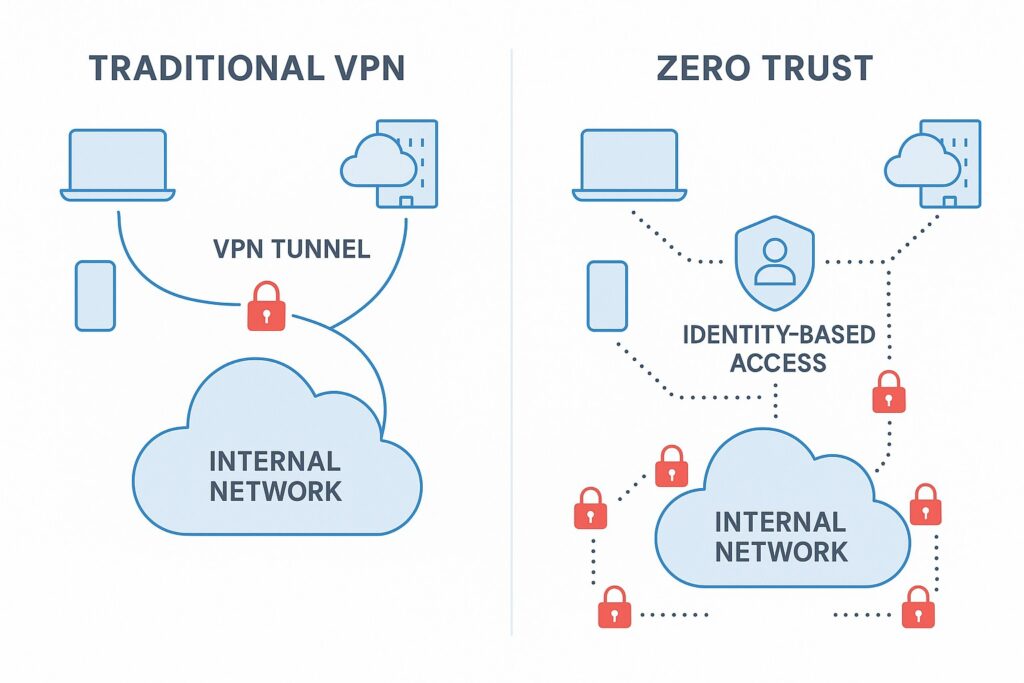
- Network segmentation and zero-trust principles to limit lateral movement
- Continuous monitoring, anomaly detection, and log correlation to identify threats
- Incident response planning, breach notification processes, and disaster recovery readiness
In intranet environments, these controls translate into permissions careful alignment with job roles, protected collaboration spaces, and rapid containment capabilities when suspicious activity is detected. Security measures should be tested and updated regularly, with governance that reflects both evolving threat landscapes and privacy obligations.
Metrics, Assurance, and Governance
Organizations need measurable indicators to assess how well privacy and security objectives are being achieved. Effective metrics tie directly to risk reduction, user trust, and regulatory readiness. Governance structures—such as privacy and security councils, policy owners, and internal audit—provide oversight and accountability. Regular assurance activities, including risk assessments, penetration testing, and privacy impact assessments, help close gaps and demonstrate improvement over time.
Key metrics often tracked include:
- Privacy impact assessment completion rate for new projects
- Time to respond to data subject access requests
- Number and severity of privacy and security incidents
- Time to contain incidents and resume normal operations
- Results of internal and external privacy/compliance audits
A mature program uses these metrics to drive continuous improvement, prioritizing initiatives that reduce risk exposure without unduly constraining business workflows. Regular reporting to leadership and to regulators, where applicable, helps maintain accountability and confidence among stakeholders, including employees, partners, and customers.
Putting It All Together: Integrating Privacy and Security
Effective data protection is not a one-off project; it is a sustained, cross-functional discipline that blends governance, technology, process, and culture. Privacy-by-design and security-by-default should be standard practices in system development, product design, and policy creation. Integrating privacy and security means aligning requirements early in the project lifecycle, conducting joint risk assessments, and ensuring that data protection is embedded into technical architectures and everyday operations.
A practical way to operationalize this integration is through iterative risk-based planning: identify data elements, classify their sensitivity, map applicable privacy and security controls, and validate their effectiveness through testing and audits. Clear ownership, documented processes, and accessible training help ensure that employees understand their roles and responsibilities in protecting personal data and sensitive information. The objective is to foster a culture where privacy and security are perceived as enablers of trust and productivity rather than as barriers to be managed.
Data protection is a design principle that should thread through every system, process, and decision.
In the end, the value of combining privacy and security lies in the outcomes: fewer data incidents, faster and fair handling of individual rights, and a stronger foundation for responsible data-driven decision-making across the organization.
FAQ
What is the practical difference between privacy and security in an intranet context?
Data privacy governs how personal data is collected, used, and shared, including rights and consent. Data security focuses on protecting that data from unauthorized access, disclosure, or loss through technical controls and governance. In an intranet, privacy ensures employees’ personal information is handled appropriately, while security ensures that sensitive information remains protected from threats and misuse.
How should organizations balance privacy requirements with security controls?
Balance comes from integrating privacy and security into the design and operation of systems. Start with a risk-based approach to determine which controls deliver the greatest protection with the least friction. Use privacy-by-design and security-by-default principles, perform regular DPIAs and threat modeling, and maintain clear policies, audits, and incident response capabilities to ensure both objectives are met without unduly hindering productivity.
What are common privacy risks for intranets and collaboration platforms?
Common risks include over-collection of employee data, insufficient data retention practices, inadequate consent or transparency around data usage, ineffective access controls, and delays in responding to data subject rights requests. Regular data mapping, access reviews, and retention schedules reduce these risks and improve both privacy and security outcomes.
How can we measure the effectiveness of privacy controls?
Effectiveness is measured through a combination of process metrics (DPIA completion rates, policy updates), operational metrics (time to respond to subject requests, incident detection and containment times), and outcome metrics (reduction in high-risk data handling, fewer data breaches). Regular audits and independent assessments also provide evidence of improvement and compliance.
What regulatory drivers should we consider when building a privacy-security program?
Key drivers include GDPR, CCPA/CPRA, HIPAA where applicable, and sector-specific standards such as PCI DSS. Consider data localization requirements, cross-border transfers, and industry guidelines that influence data handling, consent, breach notification, and vendor management. A risk-based approach helps prioritize controls that align with regulatory expectations and business needs.