Now Reading: EMV Chip Cards vs Magnetic Stripe Cards: Security Comparison
-
01
EMV Chip Cards vs Magnetic Stripe Cards: Security Comparison
EMV Chip Cards vs Magnetic Stripe Cards: Security Comparison
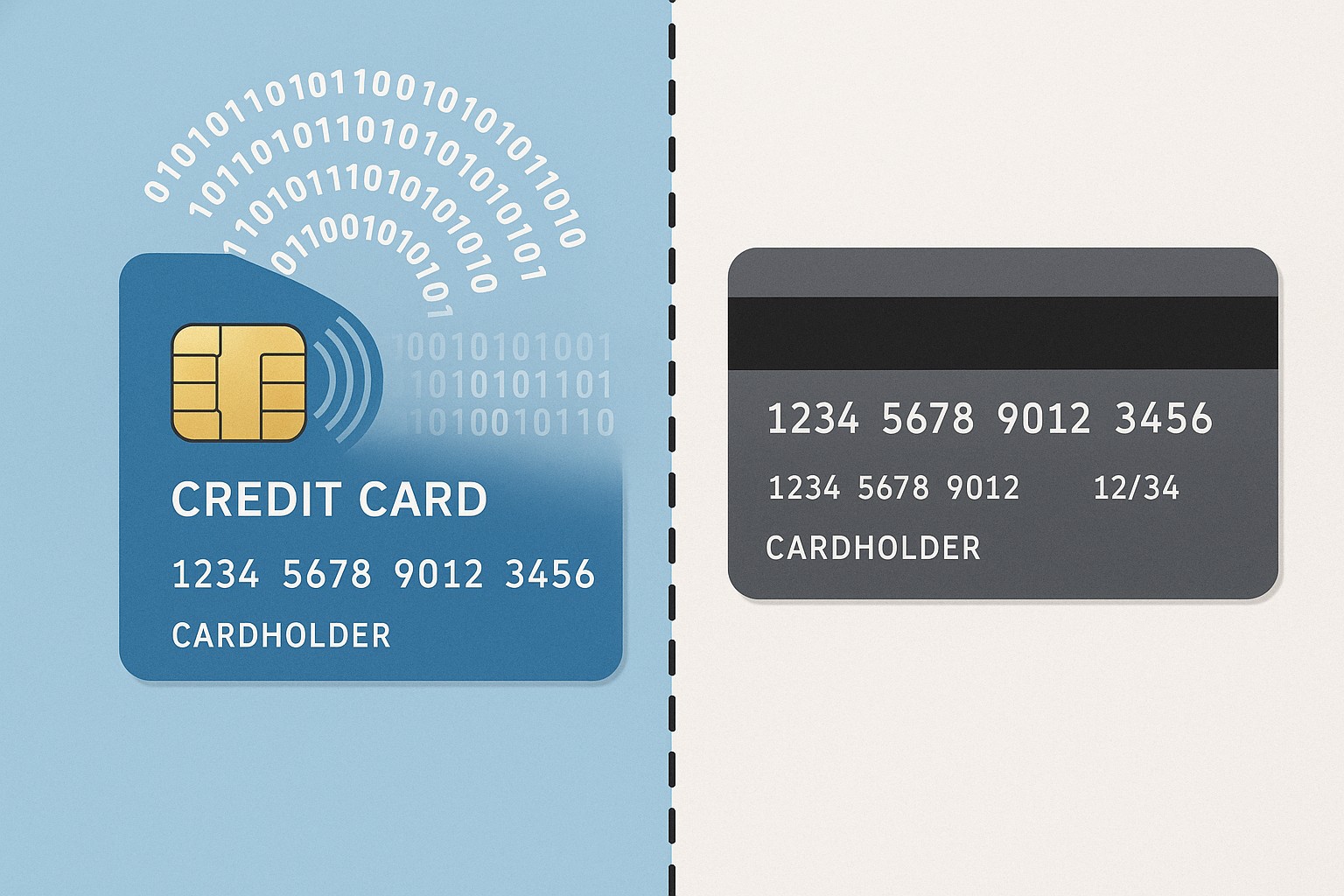
Overview of EMV and Magnetic Stripe Technologies
EMV chip cards, short for Europay, MasterCard, and Visa, embed a microprocessor chip that stores payment credentials and performs cryptographic operations at the point of sale. Unlike traditional magnetic stripe cards, EMV devices generate unique transaction data for each purchase, which reduces the effectiveness of stolen data and makes cloning much harder. Magnetic stripe cards, by contrast, carry static data on tracks that can be read by simple skimming devices, and the same data can be reused across transactions. The practical consequence is that EMV-based transactions are inherently more resistant to certain forms of fraud, while magnetic stripe transactions are more vulnerable to data theft and counterfeit card use. In most markets, the shift to EMV is driven by the combination of card-present fraud loss, merchant liability shifts, and stronger compliance expectations from networks and regulators.
In addition to the chip, EMV supports contact and contactless interfaces, enabling quick tap-and-go payments. This broadened acceptance footprint requires compatible terminals, secure key management, and issuer support for dynamic data authentication. For merchants, the transition involves upgrading card readers, software, and in many cases their payment process flows, while consumers experience faster, and often more convenient, verification methods such as PIN entry or biometrics depending on the issuer. The result is a platform that blends hardware security, cryptographic protection, and improved risk controls with evolving consumer expectations for speed and convenience.
Security Features of EMV Chip Cards
EMV cards implement a multi-layered security model designed to protect card data from theft and to make fraud more challenging for criminals. The central concept is dynamic data; instead of static credentials, each transaction uses data that is unique to that moment, derived through cryptographic processes that involve the card, the terminal, and the issuer. This design means even if a payment terminal or a capture device is compromised, the value of captured data is limited to that specific transaction and cannot be reused to authorize other payments. In addition, the chip can support offline PIN verification, ensuring that the cardholder’s intention is verified within the card itself, independent of a network connection.
Beyond data dynamics, EMV includes cryptographic keys and algorithms that protect the payment message as it travels from the terminal to the issuer for authorization. The card can perform cryptographic calculations on its own data, and the issuer can verify that the data originated from a legitimate card and terminal. There are several modes of operation (SDA, DDA, CDA, and sometimes DDA with a dynamic signature) that provide layered defenses against cloning and tampering. The overall security posture is reinforced by secure provisioning, periodic key rotation, and secure element design that isolates sensitive material from ordinary software and devices.
- Dynamic data authentication (DDA/CDA) to verify the card and transaction in real time
- Transaction cryptograms that bind the card, terminal, amount, and time to a single authorization attempt
- Offline and online PIN verification support to prevent unauthorized use
- Mutual authentication between card, terminal, and issuer to ensure trusted participants
- Secure key management and lifecycle controls to protect cryptographic material
- Support for secure element and tamper-resistant hardware to shield sensitive data
Security Risks and Vulnerabilities of Magnetic Stripe Cards
Magnetic stripe cards rely on static data that can be copied and re-encoded with relative ease, which has historically made card cloning a persistent fraud vector. Skimming devices at the point of sale capture track data from cards as they are swiped, often without the cardholder noticing. This data, combined with easily obtained card verification values, can be used to produce counterfeit cards that work in many locations until the fraud is detected. Because the data remains the same across transactions, criminal actors can reuse it for a sequence of fraudulent purchases, leading to rapid fraud growth in a merchant’s portfolio if protection is lacking.
In addition to skimming and cloning, magnetic stripe data is vulnerable to terminal compromise and network breaches. If a POS system or payment gateway is breached, raw track data or credentials stored in temporary memory can be exposed, enabling attackers to reconstruct a large set of card credentials. The technology also suffers from an absence of robust cryptographic binding between the card, the terminal, and the issuer, which means that data can be intercepted, replayed, or manipulated with limited detection by the system. Finally, because the data on the stripe is deterministic, even small errors in data entry or capture can “lock in” fraudulent transactions, making remediation more difficult for merchants and issuers alike.
- Skimming and unauthorized capture of track data at the point of sale
- Cloning and counterfeit card creation using static stripe data
- Data breaches exposing track data or credentials in transit or storage
- Terminal and malware risks that compromise payment software
- Weak data binding that allows replay or manipulation of transactions
Fraud Trends and Industry Impact
Over time, the industry has observed a clear shift in fraud patterns as EMV adoption expands. Card-present fraud losses tend to migrate from the counterfeit use of stolen card data toward card-not-present channels and e-commerce fraud, even as in-person fraud declines in regions with widespread EMV deployment. The net effect for many merchants is a changing risk profile: while the exposure to counterfeit-present fraud can be reduced through chip adoption, other fraud vectors—such as phishing, account takeover, and online impersonation—become more prominent. This dynamic has pushed industry players to invest in fraud analytics, tokenization, and risk-based authentication that accompany EMV’s cryptographic protections to deter fraud across all channels.
From a financial perspective, the shift requires merchants to weigh the total cost of ownership associated with EMV upgrades against the ongoing reductions in fraud losses and chargebacks. The cost structure includes hardware and software upgrades for terminal fleets, software licensing, PCI compliance expenditures, and staff training. Yet the improved security controls and the more resilient processing environment can yield longer-term savings through lower chargeback rates, reduced fraud-related downtime, and higher consumer trust. For issuers and networks, EMV adoption also aligns with risk-based pricing, fraud liability shifts, and the ongoing evolution toward digital wallet and token-based payments, creating a more unified and auditable payment ecosystem.
Industry data also highlights regional variability in EMV adoption and fraud outcomes. Regions with rapid terminal refresh cycles and stringent merchant requirements typically experience more pronounced reductions in counterfeit-present fraud and improved risk control during peak shopping periods. Conversely, regions with slower modernization or limited consumer uptake of new card technologies may continue to see elevated risks in certain merchant categories. The ongoing transition to contactless EMV and to dynamic data solutions is changing both the threat landscape and the operational playbook for merchants and processors alike.
Implementation Considerations for Businesses
For businesses planning to migrate from magnetic stripe to EMV-enabled acceptance, the deployment strategy should be guided by a structured project plan that aligns with business objectives, risk tolerance, and customer expectations. The most critical success factors include selecting compatible terminals, ensuring secure key management, upgrading software, and coordinating with issuers and networks to enable proper authorization. A phased rollout can help minimize disruption, while pilot testing in high-volume locations provides practical feedback on user experience, payment flow, and reconciliation. In addition to the technical change, organizations must prepare for staff training, customer education, and updates to accounting and chargeback handling processes.
Beyond immediate costs, businesses should consider long-term benefits such as reduced counterfeit fraud, improved data protection, and the potential for richer data feeds that enable better analytics and loyalty programs. Cost considerations extend to terminal leasing or acquisition, software maintenance, risk management investments, and potential impact on interchange rates and processor agreements. Effective transition also requires governance around PCI compliance, secure handling of keys and credentials, and robust change management to keep systems current with evolving EMV specifications and security best practices.
- Assess your transaction footprint and card mix to determine the upgrade scope and prioritization.
- Plan a phased migration with clearly defined milestones, budgets, and risk controls.
- Upgrade POS terminals and payment software to support EMV, contactless, and fallback handling.
- Implement secure key management, firmware signing, and regular software updates to reduce attack surfaces.
- Train staff on new workflows, PIN verification expectations, and customer assistance requirements.
- Communicate with customers about the change and provide clear instructions for any required actions (e.g., PIN entry or contactless usage).
Operational and Financial Impacts
Adopting EMV-enabled acceptance is an investment that can produce a favorable return through a combination of fraud reduction, improved payment security, and enhanced customer confidence. While initial outlays for hardware, software licenses, and integration services are non-trivial, the long-term cost of fraud, chargebacks, and operational disruption tends to be reduced as EMV protections mature in a merchant’s ecosystem. In addition, the tokenization and PCI-compliant architecture often enable more efficient reconciliation and data handling, even as merchants transition to more digital wallet and mobile payment options.
Operationally, merchants may experience modest increases in authorized transaction times due to the additional verification steps associated with EMV, such as PIN entry or secure cardholder verification, though the user experience has improved with faster contactless and streamlined reader capabilities. From a governance perspective, the shift imposes ongoing requirements for key management, software updates, and periodic PCI validations. Overall, the security posture improves materially, and with it comes the potential for risk-based pricing, lower insurance costs, and greater resilience against evolving fraud schemes.
Future Outlook and Best Practices
The future of card payments is increasingly defined by stronger cryptography, tokenization, and a broader ecosystem of secure digital wallets that support EMV-based cards and their successors. Card issuers and networks continue to push dynamic data authentication, better risk analytics, and more granular controls at the point of sale. In parallel, merchants are adopting contactless and mobile-based payment experiences that leverage EMV’s secure foundations while delivering speed and convenience for customers. To stay ahead of the curve, businesses should adopt a risk-based approach, monitor for anomalous activity across channels, and align with evolving standards such as updated EMV specifications and PCI requirements.
Best practices include maintaining a refreshed, well-scoped terminal fleet, implementing tokenization for sensitive data in transit and at rest, and integrating robust fraud analytics and machine learning-based detection. Consumer education remains a critical enabler of success: when customers understand how chip and PIN, and contactless payments protect them, adoption rates rise and fraud losses decline. Finally, a disciplined approach to security governance—regular audits, key rotation, incident response planning, and vendor risk management—helps organizations maintain resilience as the payments landscape evolves.
FAQ
Below are commonly asked questions about EMV chip cards and magnetic stripe cards, addressing practical considerations for businesses and consumers alike.
What are EMV chip cards and how do they improve security compared with magnetic stripe cards?
EMV chip cards store credentials in a secure microprocessor and generate dynamic, per-transaction data that binds the card, terminal, and transaction details. This cryptographic process makes it far harder to clone a card or replay a fraudulent payment, reducing counterfeit fraud in card-present environments. In contrast, magnetic stripe cards contain static data that can be copied and reused across multiple transactions, making them more susceptible to skimming and fraud when used with compromised readers or in vulnerable environments.
Can magnetic stripe cards still be used legally after EMV adoption?
Yes, magnetic stripe technology remains supported in many markets as an adjunct to EMV, especially for certain types of consumer cards or in regions with slower modernization. However, liability shifts and network requirements increasingly incentivize the use of EMV-enabled readers and tokens. Merchants should plan to support both methods during a transitional period while coordinating with issuers and processors to minimize risk and ensure compliance.
What should a business consider when upgrading to EMV-capable terminals?
A business should assess its transaction footprint, determine upgrade scope by location and channel, and ensure terminal hardware supports EMV, contactless, and fallback handling. It should also implement secure key management, update software with current EMV specifications, provide staff training, and plan customer education. Finally, secure processes for PCI compliance, data protection, and vendor risk management should be established to sustain the security benefits over time.
How does consumer education impact EMV adoption and fraud mitigation?
Educating consumers about how chip and PIN or contactless payments work, why EMV improves security, and when to use PIN verification or token-based wallets can increase adoption rates and reduce friction at checkout. Informed customers are more likely to understand the value of the verification steps, report suspicious activity promptly, and adapt to new payment methods, collectively reducing fraud exposure and improving overall payment experience.
What are the future trends for card security beyond EMV chips?
Future trends include broader adoption of tokenization for data in transit and at rest, enhanced dynamic data authentication, stronger risk-based authentication, and deeper integration with digital wallets and mobile devices. Advances in secure element technology, biometric verification, and machine learning-driven fraud detection will continue to strengthen resilience against evolving threats, while standards bodies and networks will drive coordinated upgrades to ensure interoperability and maintain consumer protection.