Now Reading: VPN vs Zero Trust: Modernizing Remote Access Security
-
01
VPN vs Zero Trust: Modernizing Remote Access Security
VPN vs Zero Trust: Modernizing Remote Access Security
Understanding VPN-based remote access
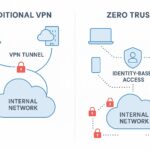
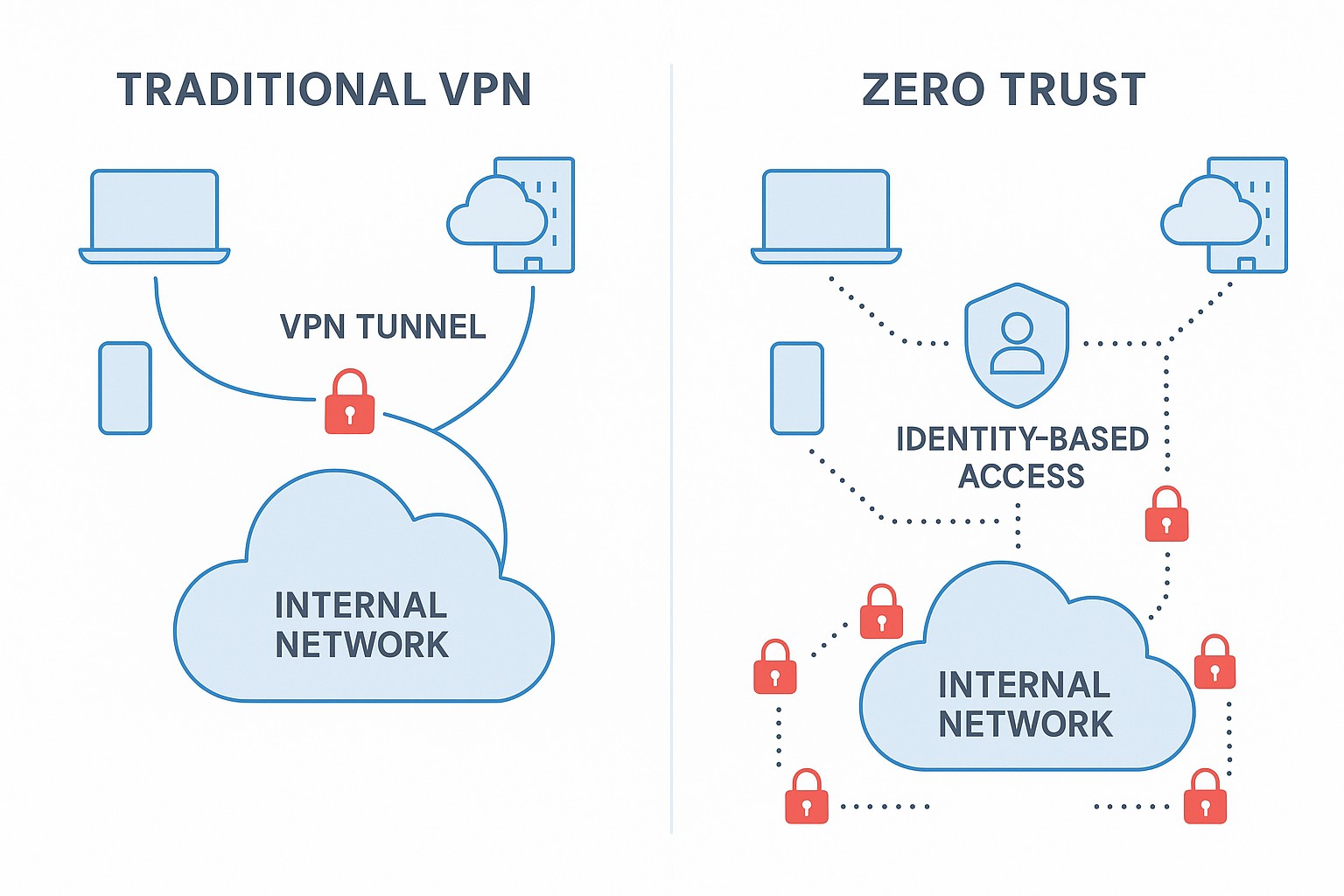
Traditional VPN-based remote access was designed to extend a trusted corporate perimeter to users outside the office. In this model, employees, contractors, and partners connect through a secure tunnel to a gateway or concentrator that sits at the edge of the network. Once authenticated, sessions often grant broad access to a large swath of internal resources as long as the user remains connected. This network-centric approach treats the trusted status of the user’s device and connection as a sufficient condition for permission, which creates a meaningful risk if credentials are compromised or a device is breached. The principal assumption is that whoever is inside the network can be trusted to some degree, which hides subtle authorization decisions behind the abstraction of “connected or not.”
In practice, VPN deployments frequently rely on static access controls, IP-based allowances, and gateway-level policies. While many VPN solutions support MFA, device checks, and centralized logging, enforcement remains largely about who is connected to the network rather than who should access which application or data set. That creates blind spots: users can sometimes reach unintended services, the level of access can be too broad, and visibility into user activity within the network is mediated by the gateway rather than by resource-level controls. The result is a mismatch between how security policy is defined (per resource) and how it is enforced (per network tunnel).
From an operational perspective, VPNs can introduce bottlenecks and friction. Remote sessions often route traffic through central endpoints, which can cause latency, degrade user experience, and complicate performance management. When multiple remote users stream to a shared corporate gateway, capacity planning becomes a constant concern, and any scaling challenge can lead to outages or degraded access during critical business windows. All of these factors drive interest in approaches that reduce implicit trust, improve granularity, and offer more responsive security without sacrificing usability for legitimate remote workers.
Zero Trust Network Access (ZTNA): a modern paradigm
ZTNA reframes remote access by shifting from a network-centric model to an application-centric, identity- and policy-driven approach. The core idea is to treat every access request as untrusted by default and to verify the user, device, and context before granting access to a specific application or resource. In practice, ZTNA typically presents remote users with a list of permitted apps rather than a full network, and it enforces least-privilege access at the resource level. This means that even after successful authentication, a user may see only a single, approved application instead of the entire corporate network, dramatically reducing the potential blast radius if credentials are compromised.
Another foundational principle is continuous verification. ZTNA systems assess multiple dimensions of trust—identity, device posture, location, time, and risk signals—from the moment a request is made and throughout the session. If the trust posture changes, or new indicators of risk arise, access can be restricted or revoked in near real time. Microsegmentation further limits lateral movement by isolating resources so that compromise of one application does not automatically expose others. The combination of identity-driven policy, dynamic risk assessment, and resource-level enforcement creates a security fabric that is more resilient to modern attack techniques while supporting flexible, remote work patterns.
From an implementation perspective, ZTNA platforms often integrate with existing identity providers and endpoint management solutions. They support gradual adoption, starting with the most sensitive applications or data and expanding to broader sets of resources as policies mature. This approach aligns with strategic goals such as minimizing business disruption, maintaining strong access controls during mergers or remote-expansion scenarios, and accelerating incident response by providing clearer signals about who accessed what and when. In short, ZTNA enables a security posture that scales with remote work without sacrificing user productivity or application usability.
Key differences: VPN vs ZTNA
The move from VPN to ZTNA represents more than a feature upgrade; it reflects a shift in governance, risk posture, and operational reality. VPNs center on establishing a tunnel that grants network access, which creates a broad trust surface and can be exploited if credentials, devices, or network configurations are compromised. This model often equates user identity with network presence, making it harder to enforce precise, resource-level controls or to monitor access in a granular manner.
ZTNA, by design, applies explicit decisions about who can access which resources, under what conditions, and with what level of certainty. It emphasizes least privilege, continuous evaluation, and context-aware decisions that adapt to evolving risk signals. Access is typically granted to specific applications or services rather than to the entire network, and sessions are constrained by dynamic policy rather than static credentials tied to a location. This paradigm reduces the blast radius of breaches, improves the ability to attribute and audit activity, and supports more precise compliance with data-protection requirements.
- Elimination of implicit network trust; access is resource-specific and context-driven rather than network-wide.
- Granular, per-application or per-resource access control instead of broad network exposure.
- Context-aware authentication and authorization, incorporating identity, device posture, location, time, and risk signals.
- Default-deny posture with continuous policy evaluation and rapid revocation capabilities.
- Reduced attack surface and improved segmentation, limiting lateral movement even if credentials are compromised.
- Enhanced visibility, telemetry, and analytics across users, devices, and resource access events.
Migration and implementation considerations
Transitioning from VPN to ZTNA should be approached as a staged program rather than a single big switch. Begin with an accurate inventory of apps, services, and data endpoints reachable through VPN, and classify resources by sensitivity, required access duration, and business impact. This mapping helps define policy boundaries that align with real-world workflows and minimizes disruption for end users. A well-documented inventory also supports risk assessment and helps prioritize which applications should be migrated first to demonstrate value early and gain executive sponsorship.
Equally important is aligning the ZTNA design with existing identity and device management ecosystems. Integrate with the organization’s IdP to ensure strong authentication and with mobile or endpoint management to obtain device posture information. Plan a phased rollout that excludes high-risk resources from initial exposure, uses pilot groups with representative workloads, and iterates on policy thresholds based on feedback and telemetry. Clear success metrics—such as time-to-access, error rates, user satisfaction, and incident response times—provide objective signals for refining the model and justifying further investment.
- Discover and inventory resources; classify required access and define per-resource scopes.
- Integrate with identity providers and device management to enforce posture checks and conditional access.
- Design microsegmentation and per-application policies; implement least-privilege access.
- Choose an appropriate ZTNA gateway architecture (cloud-hosted vs. on-prem) and plan integration with other security controls.
- Pilot with a representative user group; collect feedback, measure outcomes, and adjust policies.
- Roll out in waves by department or risk tier; monitor adoption, performance, and security events to drive continuous improvement.
Operational impact and risk management
ZTNA can deliver meaningful improvements in performance and user experience when designed with routing efficiency and localized policy enforcement in mind. Remote users benefit from faster access to specific applications without traversing entire networks, and IT teams gain finer-grained control over who can do what and when. However, the cost model for ZTNA can vary by provider, deployment mode, and the breadth of policies required, so organizations should conduct a thorough total cost of ownership analysis that includes licensing, integration, and ongoing governance expenses. It is also important to plan for adequate staffing or managed services to manage policies, monitor risk signals, and respond to incidents.
Privacy and compliance considerations rise alongside richer telemetry and identity-based access decisions. Telemetry about user behavior, device posture, and location can be sensitive, so data minimization, clear retention guidelines, and alignment with regulatory requirements are essential. Organizations should implement robust governance around data collection, storage, and sharing, and ensure access controls are in place for security teams while respecting user privacy in line with applicable laws and corporate policies. A disciplined approach to data governance helps maintain trust and reduces the risk of over-collection or misuse of personal information.
Finally, organizations should anticipate potential trade-offs during the transition. There may be initial friction as users adapt to app-level access controls and new authentication prompts, and legacy systems might require additional adapters or integration work. A well-defined governance model, explicit change management processes, and an incident response plan tailored to ZTNA scenarios will help maintain resilience and ensure the organization can respond quickly to anomalies, policy violations, or misconfigurations.
- Total cost of ownership and licensing models across cloud-first vs hybrid deployments.
- Performance considerations: latency, reliability, and multi-region scalability.
- Vendor landscape: interoperability with IdP and endpoint management, roadmap maturity, and support models.
- User experience: onboarding, authentication prompts, and ease of access to required apps.
- Compliance, auditing, and data retention policies that govern telemetry and access logs.
What is Zero Trust Network Access (ZTNA) and why does it matter for remote work?
ZTNA is a security model that grants access based on identity, device posture, and contextual risk rather than simply being connected to a network. For remote work, this matters because it reduces the attack surface, provides granular control over which applications are accessible, and enables continuous evaluation of trust throughout a session, which enhances both security and user experience for legitimate workers.
How does ZTNA differ from traditional VPN in practice?
In practice, ZTNA enforces access at the application level with least-privilege policies and continuous risk assessment, while VPNs typically provide broad network access once a user is authenticated. This shift reduces exposure, improves visibility, and supports faster incident response by limiting what users can access even when authenticated.
What are common challenges and cost considerations when migrating to ZTNA?
Key challenges include aligning identity and device posture data across ecosystems, managing policy complexity, and ensuring a smooth user experience during the transition. Cost considerations involve licensing models, integration work, potential retraining, and ongoing governance to maintain a robust security posture as policies evolve.
Can an org run VPN and ZTNA in parallel during a transition?
Yes. A phased approach often involves running VPN and ZTNA in parallel, with a controlled migration where users gradually move to ZTNA while VPN continues to serve as a fallback. This minimizes risk, preserves productivity, and allows policy teams to validate configurations and measure impact before decommissioning legacy access.
What criteria should we use when evaluating ZTNA solutions?
Evaluate based on how well the solution supports granular per-resource access control, integration with your IdP and endpoint management, scalability across regions and users, performance characteristics, ease of policy management, and the quality of visibility, logging, and incident response capabilities. Consider also the vendor’s roadmap, security certifications, and ability to align with regulatory requirements relevant to your industry.