Now Reading: Key Blockchain Protocols and How They Work
-
01
Key Blockchain Protocols and How They Work
Key Blockchain Protocols and How They Work
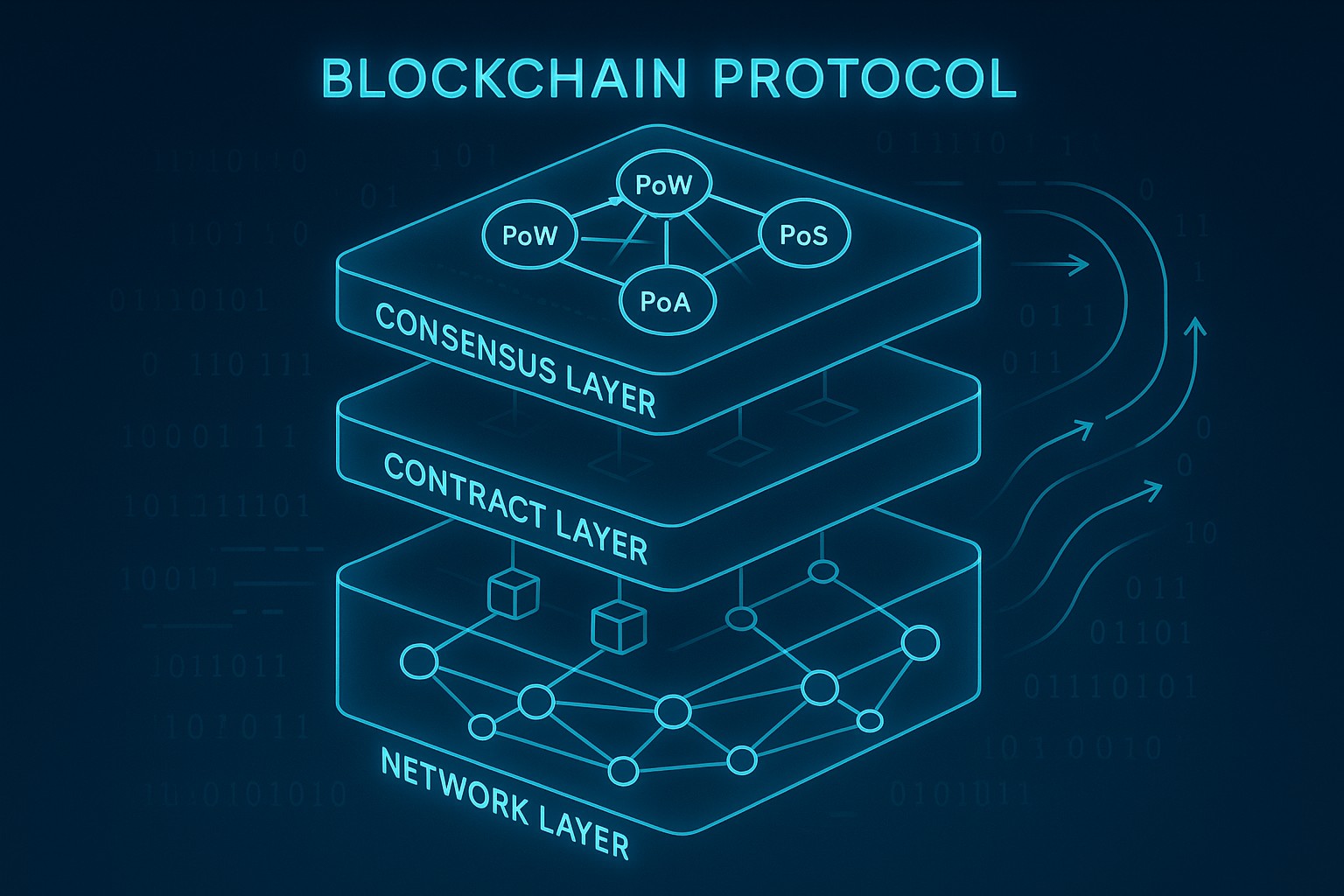
Overview of blockchain protocols and consensus mechanisms
Blockchain protocols define the rules, data structures, and interactions that allow a distributed network of participants to agree on a single, shared history without relying on a trusted central authority. These rules cover how data is organized into blocks or ledgers, how transactions are validated, how new blocks are produced, and how participants prove and verify their right to participate in the process. Beyond cryptography, protocol design encompasses networking, incentive structures, governance processes, and upgrade paths that scale as participation grows. In practice, different protocols optimize for different combinations of security, throughput, latency, decentralization, and governance complexity. The choice of protocol often reflects the intended use case—public, permissionless networks with broad participation versus private, permissioned environments used by enterprises for controlled collaboration and compliance—and it shapes how developers build applications and how regulators assess risk and accountability.
At a deeper level, consensus is the mechanism by which distributed participants agree on a single agreed record even in the presence of failures or adversarial behavior. This involves probabilistic or deterministic finality, voting or stake-based rights, and strategies for reconciling competing views of history when network partitions occur or messages are delayed. A robust protocol couples cryptographic integrity with governance rules that allow upgrades, parameter changes, and dispute resolution without fracturing the network. As networks evolve, interoperability, cross-chain messaging, and Layer-2 solutions become critical considerations, influencing how new protocols interoperate with established ones and what it means to move assets, data, or identity across ecosystems.
Proof of Work (PoW): Mechanisms and trade-offs
Proof of Work remains the archetype for public blockchain consensus. In PoW systems, network participants—the miners—compete to solve a computational puzzle whose difficulty adjusts to maintain a steady cadence of block production. The first miner to produce a valid proof broadcasts a new block, which other nodes validate and then extend the chain by appending the block with the heaviest believed evidence of work. The security model assumes that an attacker would need to control a majority of total mining power to rewrite recent history, which becomes prohibitively expensive as the network grows. This design creates a robust deterrent against tampering but imposes substantial energy costs and can concentrate mining power in large pools or regions with cheap electricity. These dynamics shape network resilience, distribution of influence, and the long-term sustainability considerations that enterprises and policymakers weigh when engaging with PoW networks.
- Hash power as the primary security resource: block validity is contingent on demonstrated computational effort rather than a stake or identity.
- Difficulty adjustment and block cadence: the puzzle difficulty adapts to keep blocks produced at a predictable rate, stabilizing confirmation times under varying network load.
- Incentive structure: miners are rewarded with newly minted coins and transaction fees, aligning economic activity with network security and maintenance.
- Trade-offs: energy intensity and potential centralization of mining power raise concerns about governance, censorship resistance, and environmental impact, influencing regulatory and investor considerations.
PoW networks promote broad participation and strong security properties through economic incentives, but their energy footprint and exchange-rate volatility of rewards can complicate enterprise planning or long-term visibility. As public networks mature, many builders explore transitions to alternative consensus models or layered solutions designed to preserve security while improving efficiency and sustainability. For institutions evaluating PoW ecosystems, factors such as liquidity, ecosystem maturity, available tooling, and alignment with sustainability goals become decisive in choosing where to build or participate.
Proof of Stake (PoS) and its variants
Proof of Stake shifts the security foundation from energy expenditure to stake-based participation. Validators lock a stake of the network’s native asset as collateral and gain the right to propose and vote on blocks according to rules that probabilistically or deterministically favor those with higher stake and longer-term commitment. The core idea is to align financial incentives with network health: validators have more to lose from misbehavior than casual participants, and the cost of attacking the network is the potential loss of staked collateral. PoS generally reduces energy consumption and can enable faster finality and more flexible governance. However, it also introduces new risks related to stake distribution, validator governance, and the handling of forks or misbehavior, which need careful design through slashing conditions, finality gadgets, and reward structures.
- Staking and validator selection: participants lock assets to become validators, often with rotating or pseudo-random selection to produce blocks and votes.
- Slashing and accountability: misbehavior such as double signing or equivocation can lead to stake penalties, enforcing economic discipline in the validator set.
- Finality and liveness properties: many PoS systems target fast finality through voting rounds or BFT-like progress checks, with probabilistic or deterministic finality guarantees.
- Variants across ecosystems: networks differ in how they implement finality, governance, delegation, and validator participation—ranging from pure PoS to hybrid models that incorporate elements of PoW or delegated proof of stake (DPoS).
Across ecosystems, PoS variants address the need for energy efficiency, rapid upgrades, and inclusive governance while also shaping risk profiles, such as stake centralization, validator hardware requirements, and the design of slashing and rewards. In practice, large networks pursue a mix of approaches: some emphasize rapid finality and human-readable governance cycles; others prioritize broad decentralization and reduced reliance on a small number of validators. Enterprises evaluating PoS options typically consider the security model, the distribution of stake and validators, the quality of tooling for node operation, and the maturity of cross-chain interoperability and compliance features. For developers, PoS often provides a more predictable upgrade path and more controllable performance characteristics compared to PoW, though it requires disciplined design around staking exposure and validator economics.
Beyond PoW/PoS: BFT-inspired and alternative consensus protocols
Byzantine Fault Tolerant (BFT) inspired consensus protocols, such as Practical Byzantine Fault Tolerance (PBFT) and its modern derivatives, offer fast finality with strong safety guarantees in networks with a known set of validators. PBFT relies on a quorum-based voting process where honest participants confirm messages and blocks through multiple rounds, enabling a transaction history that becomes final after a bounded number of steps. In practice, BFT-inspired systems are popular in permissioned or consortium settings where participants are known, vetted, and trusted to some degree, allowing predictable performance, low latency, and robust security under defined fault models. This family of protocols also informs the design of more scalable variants that aim to retain fast finality while accommodating larger, partially trust-minimized networks.
Modern BFT-like implementations such as Tendermint and HotStuff blend traditional BFT guarantees with cryptographic techniques and modular network components. Tendermint, for example, couples a BFT-style consensus with a proof-of-stake or permissioned validator set to deliver near-instant finality for simple, predictable workloads, while HotStuff focuses on a streamlined pipeline and simplified leadership changes to improve fault tolerance under higher network load. These protocols excel in environments where governance is centralized or semi-centralized, where predictable latency is critical, and where regulatory or enterprise requirements favor explicit validator identities and auditable participation records. They also influence cross-chain design by providing paradigms for fast, deterministic finality that can be integrated into multi-chain ecosystems, sidechains, or layer-2 solutions with different security premises.
Alternative protocols and mechanisms
Beyond PoW and PoS, several other distributed ledger technologies and protocol families address different performance, governance, and interoperability needs. DAG-based approaches, such as IOTA’s Tangle or similar directed acyclic graph designs, eschew a traditional linear chain in favor of a graph structure that enables parallel validation of transactions. These models can offer high throughput and low transaction costs in certain use cases but often require different security assumptions and coordination mechanisms. Hashgraph, which uses a gossip-based protocol with virtual voting, claims high throughput and strong asynchronous fault tolerance, making it appealing for enterprise contexts that prioritize speed and determinism while managing trust relationships among participants. Avalanche, with its Snow family of consensus mechanisms, offers urgent finality and sub-second confirmation times across potentially thousands of validator nodes, supported by a flexible subnet architecture that enables multiple interoperable blockchains to operate within a shared security model. Each of these families trades different guarantees—such as finality timing, network assumptions, or governance structure—for specific performance or scalability goals, and they are increasingly considered in multi-chain strategies and cross-chain interoperability projects.
Industry observers increasingly view these alternative protocols as complementary to traditional PoW/PoS networks. They enable specialized use cases—such as high-frequency microtransactions, private enterprise workflows, or multi-chain ecosystems—while still seeking alignment with broader asset custody standards, regulatory expectations, and standardization efforts. For developers and operators, the choice among these protocols depends on throughput targets, latency requirements, validator and governance models, security postures under realistic threat assumptions, and the ability to integrate with existing IT stacks and compliance programs. In many cases, organizations adopt a pragmatic mix: public PoW/PoS networks for permissionless innovation and cross-border liquidity, together with private or consortium protocols for sensitive workflows, before considering cross-chain bridges and interoperability layers to connect disparate ecosystems.
Industry applications and deployment considerations
Businesses evaluate blockchain protocols against practical deployment criteria that include performance, governance, data privacy, and regulatory alignment. Financial services firms, for example, often demand fast finality, auditability, and robust access controls, which makes BFT-like PoS or permissioned PoS solutions attractive for settlement rails, trade finance, and know-your-customer/data privacy regimes. Supply chain networks value traceability, provenance, and immutable audit trails, where transparent data sharing must coexist with permissioned access and confidentiality. In healthcare and pharmaceuticals, distributed ledgers can support secure patient consent management, tracking of immutable records, and compliance with privacy regulations, while gaming and digital asset platforms prioritize low-latency microtransactions and efficient dispute resolution. Across these sectors, interoperability with existing ERP, CRM, and regulatory reporting tools is a critical consideration, as is the ability to operate validator infrastructure in diverse geographic regions and under evolving data sovereignty requirements.
From a technical perspective, deployment decisions hinge on several factors: the desired security model and threat assumptions, the expected transaction volume and latency targets, the governance structure and upgrade path, and the operational considerations around validator availability, staking economics, and node maintenance. Enterprises also assess ecosystem maturity, tooling for development and monitoring, and the availability of robust compliance and risk-management capabilities. Interoperability strategies—such as cross-chain messaging, bridges, and sidechains—introduce additional layers of complexity but are increasingly essential for connecting disparate networks and ensuring liquidity, asset portability, and unified identity management across ecosystems. In sum, the protocol choice is driven by a blend of security guarantees, performance needs, governance preferences, and a company’s broader digital strategy and regulatory posture.
FAQ
What is a blockchain protocol?
A blockchain protocol is the set of rules and algorithms that govern how a distributed ledger operates. It defines data structures (blocks, transactions, and their formats), how consensus is reached, how new participants join, how validators or miners are selected, and how upgrades or governance decisions are implemented. Different protocols implement different consensus mechanisms and incentive models, which in turn influence performance, security, scalability, and regulatory considerations across applications and industries.
How do PoW and PoS differ in terms of security and energy use?
PoW relies on computational work as the primary security resource, requiring significant energy consumption to deter tampering and maintain the integrity of the chain. Its security scales with total hash power, but environmental impact and potential centralization of mining power are ongoing concerns. PoS replaces energy expenditure with stake-based participation; validators lock assets as collateral and gain rights to propose and vote, with penalties (slashing) for misbehavior. PoS generally consumes far less energy and can offer faster finality, but introduces different governance dynamics, stake distribution risks, and the need for robust validator incentives to maintain decentralization and liveness.
Which protocol is best for enterprise use?
There is no one-size-fits-all answer. Enterprise deployments often favor deterministic finality, predictable performance, and strong access controls. BFT-like PoS or permissioned PoS networks are common in supply chain and financial services because they offer fast, auditable finality and clearer governance structures. Public PoW or PoS networks are suitable for open collaboration and broad interoperability when regulatory and security considerations align with a permissionless model. The optimal choice depends on the required risk model, data privacy needs, regulatory constraints, and the organization’s ability to operate validator infrastructure or participate in staking programs.
Will new protocols replace existing ones, or will networks evolve to support multiple consensus models?
The trajectory is toward a diverse, multi-model ecosystem in which different networks and layers address distinct workloads. Some projects combine consensus approaches (for example, PoW or PoS security with sidechains or Layer-2 solutions) to balance throughput and decentralization. Others favor targeted, permissioned networks with BFT-like finality for specific use cases, while public networks continue to innovate with new protocol families to enhance scalability and interoperability. In practice, many organizations will operate across multiple models, using bridges and interoperability standards to connect disparate ecosystems while preserving governance, security, and regulatory alignment.