Now Reading: SaaS vs On-Premises Software: Pros and Cons
-
01
SaaS vs On-Premises Software: Pros and Cons
SaaS vs On-Premises Software: Pros and Cons
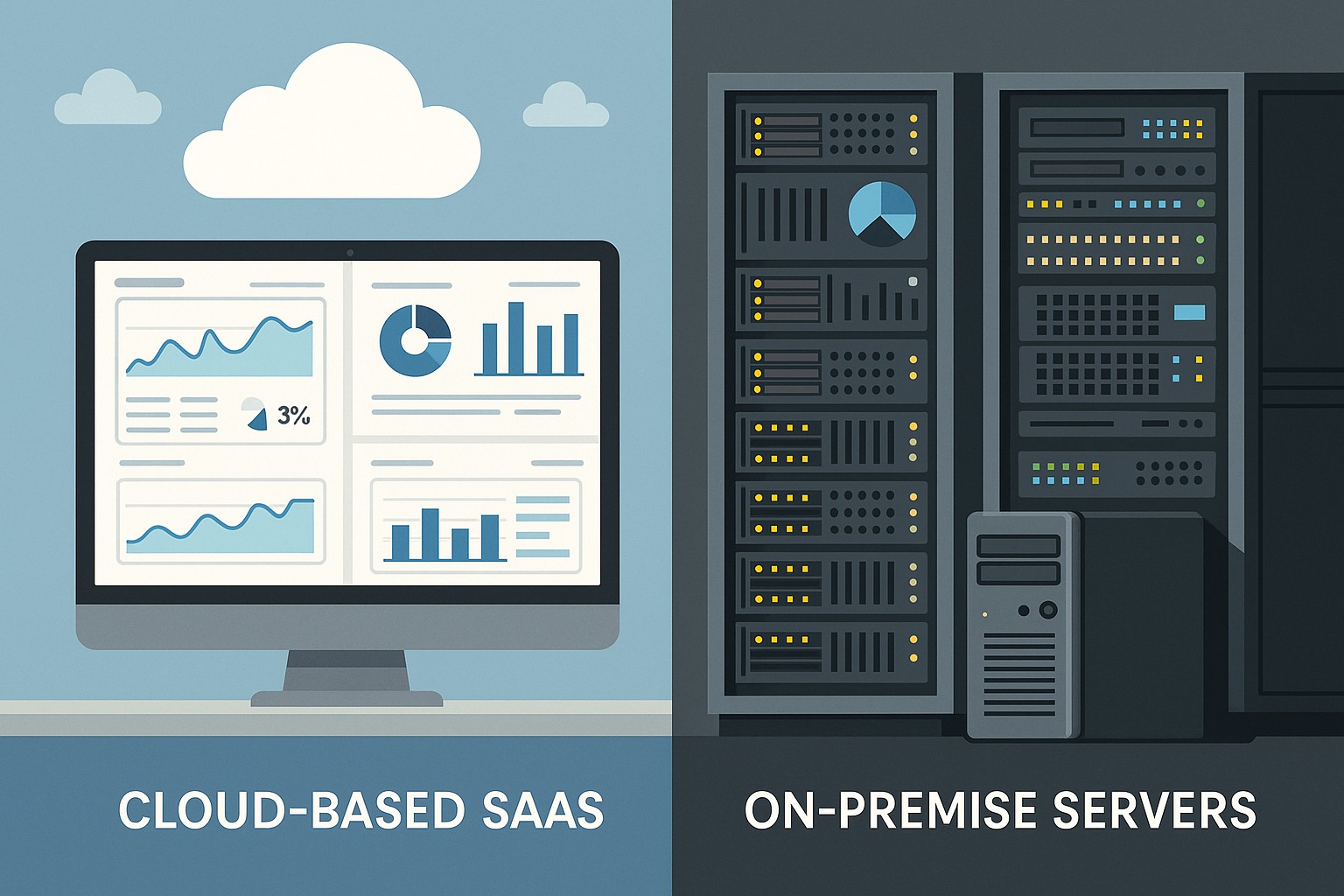
Overview of deployment models
SaaS (Software as a Service) and on-premises software deployments represent two ends of a spectrum in how applications are hosted, delivered, and consumed. In a SaaS model, the provider hosts the application and infrastructure, handling maintenance, security, and availability, while customers access the software over the internet. In contrast, on-premises software is installed locally within an organization’s own data centers or private infrastructure, giving the business full control over the environment, configuration, and updates. For many firms, the decision hinges on risk tolerance, regulatory requirements, and the level of internal IT capability to manage complex environments.
In practice, organizations choose between these models based on trade-offs between speed and control. SaaS typically enables faster time-to-value, lower upfront investments, and a predictable operating expense, whereas on-premises solutions offer deep customization, full data locality, and more granular control over security configurations and lifecycle management. The right choice often depends on industry-specific compliance needs, data governance policies, and how mission-critical the application is to core business processes.
Cost and TCO considerations
Financial modeling for SaaS versus on-premises is fundamentally different. SaaS is usually billed as a subscription with predictable monthly or annual fees that cover software licenses, hosting, and ongoing maintenance. On-premises deployments require substantial upfront capital expenditure for licenses and hardware, plus ongoing costs for maintenance, support, and internal staffing. Over a multi-year horizon, the total cost of ownership (TCO) can swing in favor of one model or the other depending on scale, usage patterns, and the length of vendor contracts.
For many organizations, the cloud path offers lower initial risk and easier cash flow, but it also introduces variability in monthly expenses tied to user counts, data volumes, and feature add-ons. In contrast, on-prem deployments tend to flatten cost volatility for some budgets but demand careful capacity planning to avoid under- or over-provisioning. Hidden costs in both models—such as data transfer fees, migration projects, integration needs, and the resources required for security and compliance programs—must be estimated with care to avoid surprises.
– Lower upfront capital investment
– Predictable ongoing expenses
– Reduced burden on IT for routine updates and hosting
– Elastic scalability aligned with demand
– Less need for in-house hardware maintenance
In practice, most firms that prioritize rapid digitization and business agility favor SaaS for its cost structure and speed, while those with strict data sovereignty or customization needs may justify the higher initial and ongoing expense of an on-premises approach.
Security, compliance, and governance
Security and compliance considerations are central to any deployment decision, but the responsibilities split differently between SaaS and on-premises. With SaaS, the service provider typically owns security of the cloud infrastructure, while customers remain responsible for securing data within the application, access management, and proper use. This shared responsibility model requires clear governance: strong identity controls, data classification, and monitoring to detect anomalous activity. Customers should evaluate the provider’s security posture, incident response capabilities, and the timeliness of patching and vulnerability management.
On-premises deployments place almost all security control in the customer’s hands, including network segmentation, encryption keys, and physical security of data centers. This level of control can be essential for highly regulated industries or environments with strict data residency requirements, but it also shifts the burden of risk management, patching, and ongoing hardening to the organization. Regardless of model, organizations should seek certifications and independent audits (for example, ISO 27001, SOC 2, PCI-DSS where applicable) and ensure that audit artifacts align with regulatory expectations.
– Data protection responsibilities differ by model (customer vs provider)
– Compliance artifacts and certifications (ISO 27001, SOC 2, PCI-DSS)
– Identity and access governance across environments
– Incident response coordination and tabletop exercises
– Physical security of data centers and application endpoints
Data residency and regulatory alignment are additional layers of governance. Some sectors require that data reside within specific jurisdictions or that certain data types never leave a particular region. SaaS providers often offer regional data centers and data localization options, but customers must verify how data is processed, replicated, and backed up to meet legal obligations. In on-prem environments, organizations can enforce their own controls but must still plan for cross-border data movement if any external services are integrated.
Updates, maintenance, and reliability
One of the most tangible differences between SaaS and on-premises is how updates are applied and who bears the responsibility for uptime and disaster recovery. In a typical SaaS arrangement, the provider manages software updates, security patches, and infrastructure resilience. This can reduce the burden on the customer’s IT team and improve reliability, since updates are often rolled out with standardized changelogs and service-level commitments. However, customers must live with the provider’s release cadence and may encounter feature changes or deprecations on a schedule dictated by the vendor.
On-premises deployments require ongoing patch management, version upgrades, and hardware lifecycle planning by the customer. This approach provides maximum control over when and how changes occur but demands more internal capacity to test, validate, and deploy updates without disrupting business operations. Data backup and disaster recovery planning remain essential in both models, yet the mechanisms differ: SaaS typically leverages provider-level DR across multiple regions, while on-premises DR is contingent on the organization’s own infrastructure and recovery objectives.
Reliability expectations should be aligned with business continuity requirements, including acceptable downtime, RPOs (recovery point objectives), and RTOs (recovery time objectives). SaaS can deliver robust resilience through multi-region deployments and standardized fault tolerance, but real-world outages can still occur. On-prem strategies must account for hardware redundancy, power and cooling contingencies, and tested failover procedures to ensure continuity during disruptions.
Customization, control, and integration
The degree of customization and integration capability often drives the choice between SaaS and on-prem. SaaS platforms excel at rapid deployment, standardization, and seamless updates but can impose limitations on deep customization. Organizations that require bespoke workflows, specialized data models, or tight integration with legacy systems may encounter constraints in configuration depth, API access, or extension points. In some cases, this is mitigated by modular architectures, enterprise APIs, and partner ecosystems, but it remains a common trade-off.
On-premises deployments offer the greatest control over software behavior, data schemas, and integration patterns. This flexibility is valuable for organizations with complex regulatory requirements, niche business processes, or extensive in-house tooling. However, deeper customization can lead to higher maintenance overhead, more complex upgrade paths, and greater risk of drift between environments. Careful governance is essential to balance customization with the ability to receive timely security updates and maintain interoperability with other systems.
– Customization depth and configuration limits
– Integration complexity and data mapping across systems
– Vendor dependency and roadmap alignment
– Total cost of custom development versus internal capability
In practice, many enterprises adopt a hybrid approach: core business processes run in a SaaS platform for speed and scale, while specialized modules or data-intensive components reside in on-prem or in a private cloud to meet unique requirements. This pattern aims to combine the best of both worlds but demands rigorous integration governance, data synchronization strategies, and a clear division of responsibilities to avoid silos and security gaps.
Scalability, performance, and operational concerns
Cloud-native SaaS solutions are designed to scale with demand, leveraging multi-tenant architectures, elastic compute, and broad geographic coverage. This can translate into consistent performance across a growing user base and rapid provisioning of new features. Yet, performance can be influenced by network latency, regional data egress, and the vendor’s underlying architecture. Customers should measure end-to-end latency for critical workflows and consider service-level agreements that reflect user location and business impact.
On-prem deployments scale through planned hardware capacity and capacity planning cycles. While this approach can deliver predictable performance in controlled environments, it often requires capital-intensive investments and longer lead times to add capacity. For global or distributed organizations, latency and bandwidth considerations become more complex, particularly when integrating with external SaaS services or cloud-based data stores. Strategic decisions may include regional data centers, edge compute, or dedicated networking to optimize performance without compromising security or compliance.
– Cloud scalability versus hardware-based expansion
– Latency, data transfer, and regional availability
– Multi-tenant versus single-tenant considerations
– Network architecture and security constraints
Ultimately, the choice of deployment model should align with how a business processes data, where critical workloads reside, and how it intends to grow. A thoughtful plan often differentiates between strategic capabilities that justify on-prem control and tactical, rapidly evolving services that benefit from cloud delivery.
Data residency and vendor ecosystem
Data residency requirements and the breadth of an ecosystem around a deployment option influence both risk and opportunity. SaaS can simplify cross-border data management through centralized controls, but it may introduce dependencies on a single vendor’s roadmap and regional presence. Organizations with strict data sovereignty obligations may favor on-prem or private cloud configurations to maintain direct control over data flows, storage locations, and access governance.
Beyond data handling, the vendor ecosystem—including partner networks, integrations, and support channels—shapes long-term viability. SaaS platforms tend to offer rich marketplaces, plug-ins, and prebuilt integrations that accelerate digital transformation, while on-prem environments rely on internal or partner-developed connectors and custom integration projects. Both models require diligence in due diligence, contract terms, and ongoing relationship management to ensure interoperability, negotiated pricing, and service continuity.
FAQ
What is the primary difference between SaaS and on-premises software?
SaaS is delivered over the internet by a service provider and typically requires minimal upfront investment, with ongoing subscriptions that cover hosting, maintenance, and updates. On-premises software is installed and operated within an organization’s own data center, giving full control over hardware, configuration, and lifecycle, but it demands more internal IT resources and capital expenditure.
How do security responsibilities differ between SaaS and on-prem?
In SaaS, the provider generally secures the underlying infrastructure, while the customer remains responsible for protecting data within the application, access controls, and user behavior. In on-prem deployments, the organization handles almost all security aspects, including network security, encryption keys, and physical data-center protection, offering deeper control but greater responsibility and staffing requirements.
What are the typical cost considerations when choosing SaaS versus On-Prem?
SaaS favors lower upfront costs and predictable operating expenses, with costs scaling with usage. On-prem requires larger initial investments in licenses and hardware, plus ongoing maintenance and staffing. Over time, TCO depends on scale, customization needs, and maintenance burdens; for some, SaaS reduces total cost of ownership, while others find on-prem more economical when data sovereignty and bespoke requirements are paramount.
How does updates and maintenance differ between the two models?
SaaS updates are managed by the provider, delivering new features and security patches automatically or on a published schedule, with some potential impact on users during rollout. On-prem maintenance is the responsibility of the organization, involving testing, patching, and upgrades to keep the system secure and compatible with other components, but providing more control over the release timeline.
What should organizations consider for data residency and compliance?
Organizations should assess whether data can reside in specified regions and how data movement is handled across borders. SaaS vendors may offer regional data centers and localization options, while on-prem deployments provide maximum control over data storage and access. In both cases, aligning with industry regulations, audit requirements, and contractual terms with vendors is essential to sustain compliance and reduce risk.